Complete Managed Cyber Security Service in Melbourne
CyberComplete
Fully Managed IT & Cyber Security Risk Management Solution
“Unify your security with a complete solution.”
With full visibility of the technologies utilised in your organisation, having your local Cyber Security Service Provider in Melbourne uncover any risks you may or may not be aware of is crucial.
We build, deploy and manage tailored, security-oriented solutions to minimise these risks and continually monitor your organisation in real-time for any malicious cyber activity. Rest assured that if any suspicious behaviour is detected, it will be taken care of immediately.
On a regular basis, our team performs complete objective cyber security reviews to pinpoint any new potential areas of exposure, and, if necessary, take quick and effective action to remedy them.
Reporting to your executive team is straightforward and to the point, so you don't have to worry about tech jargon getting in the way of understanding the risks you face.
Our service is built to identify, act and protect, so you can feel safe in the knowledge that CyberComplete has you covered. We are your one-stop shop for all your Managed Cyber Security Services needs in Melbourne.
“Through our end-to-end managed security solution, your organisation, clients, vendors, and suppliers will be provided with peace of mind. Make your days of worry and anxiety a thing of the past.”
How Does CyberComplete Work?
CyberComplete is a unified fixed price managed IT + Cyber Security solution for small to medium-sized organisations with up to a hundred (100) staff members who typically lack an internal IT team or currently use an outsourced IT or Cyber Security Provider.
CyberComplete has four core components. Each serves a specific purpose with the design that when all four components work together, your organisation benefits from an effective, aggressive, and continually updating security service that protects your revenue, customers, staff, reputation, and your relationships.
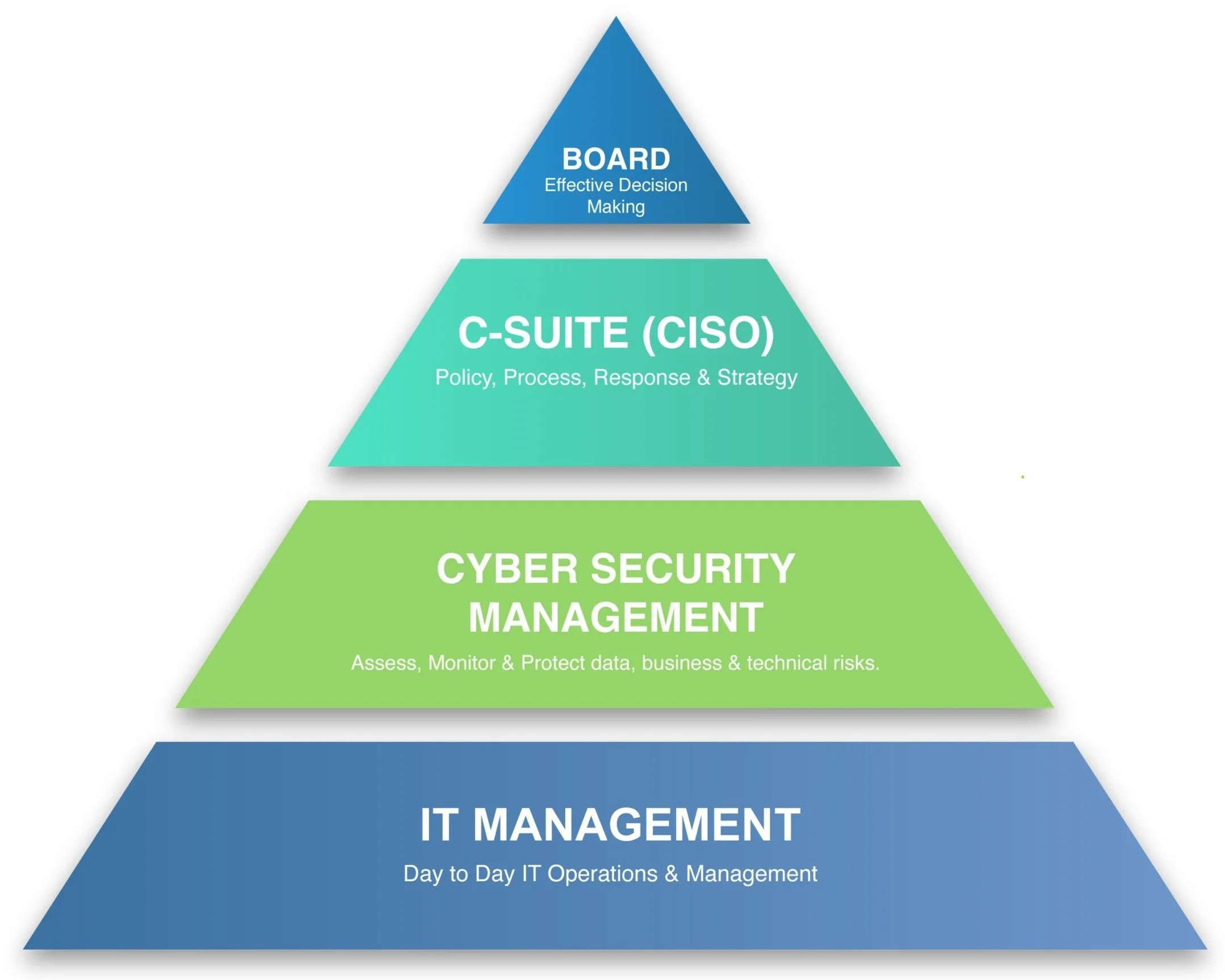
The Cyber Security Pyramid - CyberComplete
As multiple scenarios play out, you’ll notice a pattern. Events will naturally traverse this pyramid. Moving up and down.
Typically, any incident begins with staff or monitoring systems flagging or alerting to an event or incident at the IT Management stage.
Once it has been investigated and proven to be security-related, the cyber security stack is instantly the first line of protection and defence.
Following this, the CISO is engaged either by following a simple procedure, carrying out a playbook or, worst case, activating the Incident Response Plan, which encompasses informing the executive team and following the structured approach of the incident response plan.
At any point in the cycle, any incident or event can occur, which is why our CyberComplete package encompasses all four facets - visibility, process, action, and security - for guaranteed protection.
-
The Board and Directors are ultimately in charge of how much protection the organisation has against potential cyber threats. It is up to them to determine how the company should manage, react, and communicate externally if a cyber breach occurs.
CyberComplete provides critical insight to boards and directors, arming them with the knowledge they need to make informed choices that will shape the way your organisation tackles cyber security.
-
On a recurring basis, the CISO will advise the Board & Directors of any substantial business risk management decisions while creating policies and procedures that govern the organisation's technical response to a breach.
Additionally, they will oversee the examination and assessment of systems, strategies, and processes and inform everyone of the necessary laws, statutes, and compliance regulations.
CyberComplete has a dedicated Security Architect (vCISO) dedicated to overseeing your organisation's Cyber Security Maturity, ensuring your organisation is equipped with the appropriate strategies, processes and tools to protect and respond to a cyber security breach.
-
This layer introduces a highly technically advanced, specialised cyber security stack, increasing the visibility and reporting of multiple security layers. It's tailored to evaluate your technical, system and business-related risks and is also at the centre of a CISO's detection and response approach.
This layer aids the CISO in crafting and executing plans, systems, and processes to ensure the safety of the organisation, along with actively addressing potential threats and managing any existing incidents of infiltration.
CyberComplete provides a complete security stack with a number of different solutions.
Cyber Security never stops. We are proud that our Cyber Security Stack is dynamic and continually evolving to combat the latest threats and tactics.
Our Cyber Security Stack is designed to exceed the Australian Cyber Security Centre's (ACSC) Essential 8 Level 3 compliance.
-
Proper IT management and control over all company-related hardware and software components is essential. This includes the implementation of a technical support system, usually a Help Desk, as well as basic security practices, such as antivirus protection, backups, disaster recovery, and business continuity.
This layer is incredibly important as it’s the base that enables the above security layers to work effectively.
These layers of security are essential for implementing effective cybersecurity measures and for developing sound cybersecurity maturity.
CyberComplete provides a comprehensive range of IT Management solutions to ensure your core needs are met.
We'll help you manage your IT systems and resources, provide technical support for your personnel, develop strategies to leverage technology to enhance your business performance, and find innovative ways to remove roadblocks and improve operational efficiency.
What’s included in CyberComplete?
IT Management
-
95% of issues can be fixed with a quick phone call and a remote session. Give your staff the tech support they need with no costly surprises.
-
Sometimes things can’t be fixed remotely. That’s why we include onsite technical support to ensure your staff get the help they need.
-
Providing 24 x 7 x 365 monitoring and remediation for your sites & networks.
If something goes wrong, our team is alerted instantly and swing into action to minimise business disruption.
-
Managing your assets and your asset registers is a boring task no one likes to do. However, we understand the importance.
That’s why we include this in our service, so you can trust your assets and registers are always up to date
-
The boring stuff that no one likes to do. We audit all the infrastructure in your organisation to ensure it’s health is good. This allows us to catch any minor issues before they become business-critical. We also audit our monitoring systems to ensure the reported data and metrics are accurate.
-
Not just backup software. We provide an end-to-end solution that includes an onsite backup appliance, replication of data to secured Australian data centres, 24x7x365 monitoring and yearly disaster recovery testing.
To ensure your critical infrastructure is protected and readily restorable.
And even if the unthinkable happens, we are on standby to help you recover and ensure your business is operable in disastrous times.
-
We understand there are some workstations that are critical to operation. These need to be backed up. We provide the required backup solutions to ensure this occurs. Either strictly on premise backups, cloud only backups or hybrid.
-
Microsoft and Google state in their terms of service they are not responsible for your data in the event of a disaster.
We provide cloud backups for all our clients to make sure in the unlikely event these vendors lose data you’re covered.
-
The impact of the pandemic on businesses has been immense and only highlighted how fundamental technology is for them to survive and thrive. To facilitate that, we collaborate with our clients to unify services, offering an array of mobility solutions so they can be connected no matter where they are. Amongst these is integrating the telephone system into Microsoft Teams to provide true team collaboration and reduce reliance on physical handsets.
-
Are you having difficulty maintaining company policies, applications, and configurations on your workstations and laptops? Our team can help. Through the use of Microsoft Intune (Endpoint Manager) we ensure your new technology assets are provisioned with ease with a true Zero Touch approach.
Get rid of those tedious wait times for your MSP to finish manual configurations, and start chatting to our team to learn how Microsoft Intune can support your business mobility.
Cyber Management
-
You won’t see many Managed Services Providers (MSPs) or Managed Security Services Providers (MSSPs) openly state their compliance levels.
We care about our clients, and we want them to know what we’re doing and attach it to something tangible.
-
Hackers don’t sleep. Anyone that states you don’t need 24x7 monitoring is wrong. Often hackers will act on long weekends or extended breaks.
We make sure you’re protected 100% of the time.
Don’t be fooled by other providers “24x7x365 monitoring” when it’s a simple workflow. Our team 100% local Aussie security team are monitoring 24x7x365. If we see something our team will jump into action to secure your systems and data.
Our team monitors your endpoints, your cloud apps, your networks and your backups for any signs of malicious activity.
-
So secure if you lose your master key and recovery questions, we can’t get your data back. Is that bad? No!
This means hackers do steal your password vault; they still cannot access your data or decrypt it.
-
AI-powered email security offers reliable protection against malicious emails, such as phishing and spam. Instead of depending on fixed rules, like conventional filters do, these advanced solutions apply machine learning techniques to recognise and deflect even the most intricate cyber assaults. The capability to analyse and gain insight from vast quantities of data in real-time makes this type of security measure especially effective.
-
Protecting sensitive information shared through email is crucial, and that's where email encryption comes in. Without encryption, messages can be accessed by anyone, which could lead to a data breach, identity theft, and other security threats.
We understand most businesses won’t want or have a legal requirement to encrypt emails, however we still want to offer this as a standard inclusion.
-
MDM solutions offer a reliable way to guarantee the safety of mobile devices and the confidential data they contain. Businesses that utilise MDM have the capacity to enforce passwords, erase data from lost or stolen devices, and oversee access to corporate assets, applications, and information. In doing so, it significantly lowers the possibility of a data breach, theft, or loss of valuable information.
We believe every business should be implementing and using an MDM platform.
-
Advanced AI Web filtering is a highly effective tool. Through leveraging vast amounts of data and utilising advanced machine learning techniques, AI can rapidly and accurately recognise and respond to cyber threats quicker and more accurately than ever before.
-
Through implementing cyber security awareness training, businesses can create a culture of security and significantly reduce the chances of a breach due to human error. By educating employees on potential risks and how to address them, companies can effectively minimise their risk of cyber attacks and fortify their operations.
-
By locating where confidential information is held, organisations are better able to comprehend the threats related to that data and build adequate risk management procedures. This includes recognizing and managing possible risks such as cyber intrusions, unauthorised access to data, or sabotage by internal personnel.
-
Do you want to give your staff the ability to install certain apps, yet not give them full administrative access? Introducing Application Ringfencing. With its pre-defined policies, you can grant your employees the right to install and run approved applications. Moreover, you can use Storage Ringfencing to further restrict data transfers to external devices and exercise greater control over them.
-
It is an unfortunate fact that software-as-a-service businesses and websites are regularly hacked. Unfortunately, this is something we are unable to stop, yet we can remain vigilant. We continuously scan the dark web for newly exposed staff credentials, and if alerted, we act promptly to reset the passwords and enforce unique credentials using our password manager for maximum security.
-
Despite our highly secure protocols, no one can guarantee absolute cyber safety. The landscape of digital threats is constantly changing, so our vigilant team continuously monitors for signs of attack, taking immediate action to ensure your company remains unharmed.
Executive Strategy - CISO
-
The Security Stack is only as secure as the strategy that goes with it.
We include a “Security Architect” for all our clients. This role is dedicated to ensuring the Cyber Security Strategy is implemented, reviewed and effective for your business.
-
The CIO is responsible for aligning IT strategy with the overall business objectives of an organisation, managing the company's IT infrastructure and applications, and identifying opportunities for innovation and growth. Additionally, they must ensure the company's IT systems are secure and protected from cyber threats.
Our team works to help you achieve the core responsibilities of a CIO internally. Typically in an enterprise environment, the CIO and CISO work closely together.
-
Our team will work with you to provide an in-depth evaluation of your existing IT and security protocols. Through our thorough assessment, we can pinpoint any potential risks and provide suggestions for policies and processes that will reduce said risks.
This way, we can ensure your operations are backed by well-structured, documented procedures and controls.
Once implemented these are audited regularly to ensure effectiveness.
-
On a quarterly basis, we examine every security system and control, and we cannot presume that everything is always in order. To gain total assurance, we conduct assessments by hand and scrutinise the whole security framework to ensure it's operational and effective.
As part of our transparent reporting, we provide these results to you as well as a remediation plan to ensure action is taken and your security protections are only improving.
-
Something you won’t hear or see other Managed Service Providers (MSPs) or Managed Security Service Providers (MSSPs) do.
We work with you, your staff and your suppliers to put in a structured plan and playbook for if your business is hit with a cyber incident.
Why is this important? Having a plan and framework retains and builds trust with your customers in the event of a breach.
-
Through our stategic partnerships, we have an ear on the inside of several organisations & governments so we know and understand what legislation is in place and what legislation is coming.
Why? So your cyber security protections are compliant.
-
During our periodic evaluation process, we will sit down with you to address any discovered issues and assess the necessity of any further safeguards or modifications to guarantee your cyber security remains updated and effective.
-
Making your technology work for your roadmap to growth. We help you achieve the path and growth your business needs by reviewing and planning new technology to suit your needs
Board & Directors
-
Fully grasping cyber security can be an intimidating task, and the challenge increases when it comes to communicating the information to board or directors. That is why we provide regular updates and training to your board and directors in the area of Cyber Security.
After all, they are ultimately responsible for the decisions on matters concerning Cyber Security.
We strive to ensure your board have all the relevant information they need to make an informed decision regarding Cyber Security.
-
Our team can provide your board with periodic security briefings that are not heavily focused on technical aspects, guaranteeing they are informed of any current and future threats, as well as the latest information on cyber safety.
-
Cyber Security may not be everyone's strength, but it is vital in order to guarantee that the correct decisions are being made within an organisation. As a part of CyberComplete, we provide further instruction to your Board & Directors following the Australian Institute of Company Directors (AICD) Cyber Security Principles. Education is the most reliable means of prevention.
FAQs
-
Absolutely!
It's disheartening to know that many Managed Service Providers and Managed Security Service Providers consider Macs to be “too difficult to manage”.
Our team have come up with a variety of solutions that enable the seamless integration of Mac workstations and iOS devices into a business environments. Rest assured, Mac’s and iOS devices are fully covered by our managed security solutions.
Reach out to our team today to discuss how we can help improve your Mac fleet!
-
Yes, however, we find, typically, once an organisation grows past 100 staff, an internal IT manager is brought in to help manage the responsibility of the entire IT department.
We can still assist, but our alternative solution, Cyber365, maybe a better fit once the internal team comes on board.
-
Yes. CyberComplete complies with The ACSC Essential 8 Level 3 framework.
-
Yes, CyberComplete does include Fixed Cost IT Support as standard.
Not only do you get fixed cost IT support as covered under “IT Management”.
We also include additional services in CyberComplete so your business can enjoy increased cost savings and benefit from enhanced cybersecurity measures.
-
CyberComplete is designed to be a Unified IT AND Cyber Security Service. How the world does business is rapidly changing, and IT & Cyber Security are core components to any business technology department; that’s why we combine them. To bring the most value to smaller businesses (who are most at risk of cyber security breaches).
-
Yes absolutely.
Our minimum standard of care is ACSC Essential 8. However, we understand different organisations have different requirements (NIST, ISO 27001).
CyberComplete can scale up very quickly to meet additional framework requirements.
Reach out today to chat about the requirements you need to meet.
-
Unfortunately, no. CyberComplete is a managed IT & cyber security service designed to help businesses combat cyber security threats.
-
We totally understand. We offer a tailored service for IT managers & technology leaders called Cyber365.
Cyber365 is based off CyberComplete. However, you can tell us what layers/levels you do or don’t need as we understand you won’t need everything that CyberComplete has to offer.
-
Yes, CyberComplete can provide you with the Managed IT services you want in Melbourne.
We are a team of experienced professionals who offer advanced security solutions, scalability options and 24/7 support, ensuring your systems and data remain secure, safe and operational at all times.
With our customised and flexible IT solutions, you can reduce costs while enjoying top-level security. Let us provide you with the best in class services and technical assistance.
Schedule a call with our team to learn how CyberComplete is better than other Managed IT providers.
How do we compare to the market?
How does EvolveCloud compare to other Managed Security Services Provider in Melbourne?
Drawing on our direct knowledge of customers' environments, feedback and dissatisfaction, it is clear that our services stand out compared other service providers.
| CyberComplete | Our Competitors | |
|---|---|---|
| True, fixed price agreements with no sneaky new device costs or new user onboard costs. | ✓ | - |
| 24x7x365 Aussie based, human security team monitoring your environment in real time, not a workflow, AI or automated alerts. | ✓ | - |
| Dedicated security architect, overseeing your account, organisation & security | ✓ | - |
| Weekly, fortnightly, monthly, quarterly meetings/touch points with your security architect | ✓ | - |
| Weekly, fortnightly, monthly, quarterly onsite point of presence | ✓ | - |
| Continual updates of regulartory and legal cyber changes and requirements | ✓ | - |
| Sensitive data monitoring and reporting across your organisation | ✓ | - |
| End-to-End incident response & incident management
| ✓ | - |
| Regular, objective, and systematic cyber security reviews | ✓ | - | Transparent reporting to your C-Suite, Board and Directors | ✓ | - |
It’s hard to compare two service providers and understand the differences…
Book a call with our team, and we will help you understand what your current provider is actually providing you (compare apples to apples).
We will help you get past all the acronyms and technobabble and help you understand how our services compare and how we can better secure you.
Protect your present and secure your future with CyberComplete.
The most important step to achieving cyber resilience is taking the first step.